Politics and puzzles—it’s an irresistible pairing that takes center stage in the new Advanced Studies and Research (ASR) course at Colorado Academy, Cryptography in History and Math. Delving into the fundamental mathematical principles that underpin modern cryptographic techniques as well as their historical context, this Upper School offering is a model of just how far CA’s ASR designation aims to push the boundaries of advanced high school course work.

Why cryptography? “I thought it would be fun,” is how Upper School math teacher and Math Department Chair Dr. Michael Huntington describes what went through his mind when he first conceived of the class last year.

Huntington, who is leading the two-trimester course for Juniors and Seniors alongside co-teacher and Upper School Social Studies Department Chair Liz Sarles, clarifies, “I don’t mean the cryptography—no one does that for fun. It’s because of history that codes and ciphers even came about: I want to keep something secret, I want to communicate it, but my enemy wants to find out what that message is, so they crack my code, and then I have to design a new way to keep my secret. It’s an ebb and flow that has been tied to political and military power throughout history.”
The fun, Huntington underscores, is in the back and forth. Or, as Sarles puts it, “In social studies, we spend a lot of our time looking at turning points through different lenses: leadership or social movements, for example. You can look at major turning points through the lens of mathematical advances in encryption, too, and how history fueled those, and then how the math in turn shaped history. That’s fun to study, and it’s also fun to teach.”
Bletchley Park: A model
CA’s ASR initiative came about, in part, as a way to enable faculty members to mine their own areas of expertise and interest and turn them into unique course offerings that could inspire deep, student-driven inquiry in areas such as the humanities, computer science, and the arts. Cryptography in History and Math is more or less a “poster child” for this approach to curriculum innovation, highlighting the inherently creative, interdisciplinary weaving-together of fields that characterizes ASR.
With Huntington and Sarles literally teaching side by side, the typical class session in cryptography is “50-50,” says Sarles: an even split between math and history. “It’s completely interwoven—it has to be.”

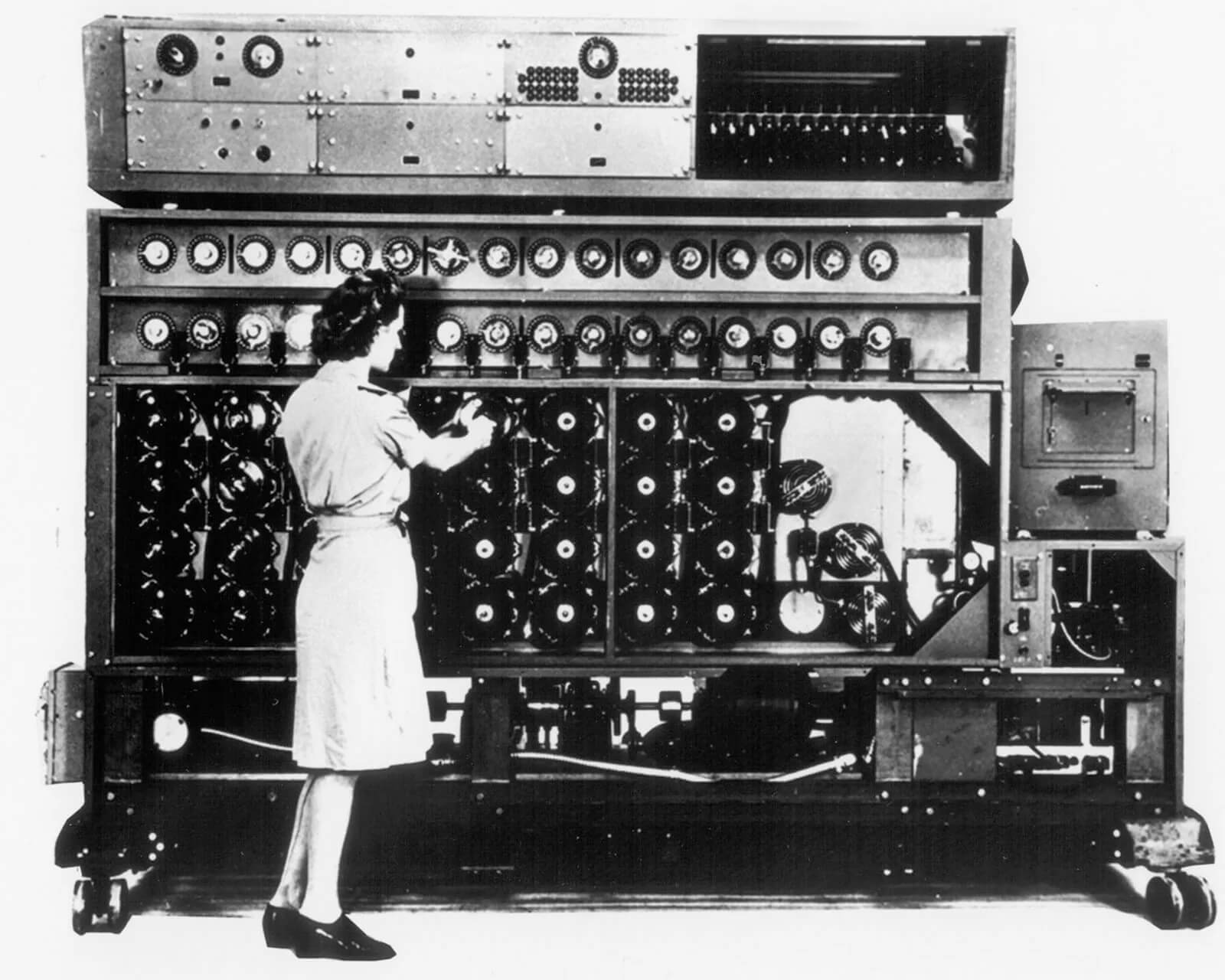
Take the example of the World War II “Enigma machine,” Nazi Germany’s military cypher device that was considered impenetrable—until Allied forces, tutored by Polish cryptologists who provided foundational materials to the famous British decryption group at Bletchley Park, broke the Enigma code in an effort that likely altered the war’s outcome.

Bletchley Park, points out Huntington, brought together “mathematicians, historians, classicists, linguists, chess players, computer scientists, and many others,” with the shared goal of penetrating the secret communications of the Axis Powers. At the home of Britain’s Government Code & Cypher School, a group of 10,000 workers, many of them women, deployed their diverse range of skills to decode valuable military intelligence that practically laid bare the entirety of Germany’s war planning.
In the classroom where Huntington and Sarles teach, the story is much the same. There are the students who are there for the “pure math,” and then there are those with an interest in language, political history, or the arts. Participants are grouped together at random to research historical ciphers and complete encryption challenges, and, Huntington notes, they quickly learn that math alone cannot do all the work. The unique individuals who collaborate to solve a problem, the different aptitudes and perspectives they bring to the table, are where the real power lies.

The simplest cipher
The course syllabus begins well before the invention of the Enigma machine or other relatively modern technologies. Cryptography in History and Math starts with what might be considered “the easy stuff”—the Caesar cipher, one of the simplest and most widely known (and least secure) encryption methods in the world.

The Caesar cipher, named after the Roman general who deployed it with so much success decades before the birth of Jesus, is easy to understand and easy to decode because it merely substitutes one letter of the Latin alphabet for another letter that is a fixed number of characters away. “The first challenge we gave our students in class was to encode and decode a message using the Caesar cipher,” explains Sarles. “They got it in a few minutes.”
Nonetheless, the cipher played a central role in Caesar’s triumphs as a military leader and statesman, and it remained the world’s dominant model for encryption for hundreds of years. By the time of the Renaissance in Europe, breakthrough work by Arab mathematicians on frequency analysis had revealed the weaknesses the Caesar cipher shared with other monoalphabetic ciphers, and polyalphabetic encoding schemes gained favor as political competition and religious revolutions intensified.
Polyalphabetic encryption substitutes the letters in a message with variable sets of letters, numbers, and symbols. Students experiment in class with one example, the cipher of Mary, Queen of Scots, which the would-be monarch used unsuccessfully while imprisoned to approve a plot to assassinate Queen Elizabeth I. At stake in this case was the outcome of the battle between England’s Protestant ruling order and the Roman Catholic church, which was to be restored to power with Mary as rightful heir to the throne.

Advances in both cryptanalysis and cipher design accelerated further during World War I and World War II, and finally, after exploring the fascinating story of how World War II’s Enigma machine cipher was cracked, students reach what Huntington calls the biggest revolution in cryptography in 150 years—the rise of algorithmic encryption, which uses number theory to convert any kind of information into digital gibberish and then back again. Even better, he notes, this modern form of encryption no longer relies on a key shared between message recipients to decode it, a fundamental weakness of all cipher schemes that preceded it.
“The math for this had been sitting there for hundreds of years,” he explains, “but no one thought to use it until the late 1970s and 1980s.”
A math explosion
Asymmetric or public-key encryption, as it is variously known, enables the secure digital communications that drive nearly every aspect of the modern world, from banking and commerce to microchip manufacturing and military and government operations. Two-factor authentication on Amazon.com is an example familiar to almost anyone.

At this point in the curriculum, which takes months to reach, however, “The math is not the same,” says Huntington. “There are students in my Advanced Topics in Math course, students taking Honors Calculus, but this is number theory.” Number theory is the study of prime numbers as well as the properties of mathematical objects constructed from integers. “It’s not that complicated: You’re still multiplying, adding, subtracting, dividing, squaring, cubing. If you could factor large numbers fast enough you could break the encryption that we have today.”
What this section of the class makes clear, Sarles continues, is that Cryptography in History and Math is designed as “an explosion of how people conceive of math. Deduction and logic—these are all forms of math. When these students are doing New York Times word puzzles, that’s math.”
“High schoolers often don’t see that there’s math outside of calculus,” Huntington observes. “But there’s a whole practical field out there that’s incredibly compelling.”
And it goes beyond even math and computer science, they emphasize. During World War II, the Enigma cipher was discovered to be vulnerable, not as a result of brute-force mathematics, but due to human error and flawed operating procedures that inevitably broke down during wartime, along with the efforts of spies who were able to obtain German reference materials.
“I am a huge believer in thinking about history, thinking about almost anything, in an interdisciplinary way,” explains Sarles. “Anytime we can ask our students to look outside of the narrow confines of a single discipline, we are encouraging higher-level critical thinking—more like what they’ll be expected to display in college.”
That’s not to mention the benefits of seeing two teachers approaching a subject from completely different perspectives, and succeeding in creating something that’s surely greater than the sum of its parts.
“Here we are, working together, and everyone knows that there’s a lot of the math that I can’t do,” Sarles acknowledges.
“And the discussions about history often leave me in the dust,” adds Huntington.
In other words, continues Sarles, “The two of us are willing to sit with things that are uncomfortable, accept where there may be gaps in our knowledge, and yet still be able to say with confidence that, like our students, we are truly and deeply engaged in learning together.”